Problem
ABB Traction – a local business unit of ABB Switzerland – develops among other products control units which are used in the field of voltage conversion. Depending on the application, they interact with power electronic devices in trains, power plants and wind turbines. Both the proximity to people and the high voltages to be processed create a potential hazard that must not be neglected. In particular, the fact that a large part of the population depends on the correct functioning of these devices for applications such as national power generation and public transport makes them particularly worth protecting. In order to be able to guarantee this protection, it must be guaranteed that only software from trustworthy sources is executed on these devices. In addition, one must be sure that it has not been tampered with.
Root of Trust
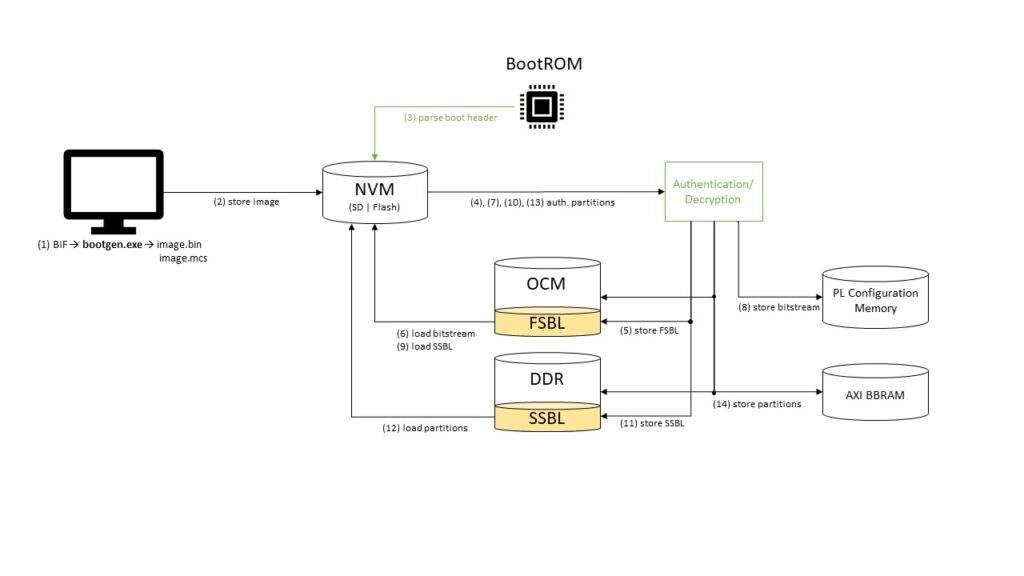
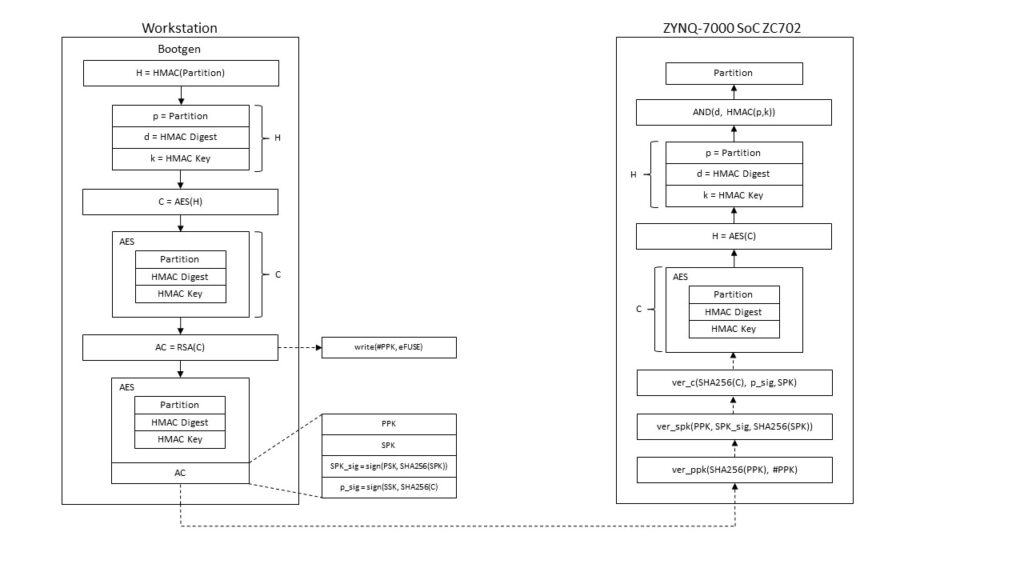
The term root of trust describes a practice in Software Design aimed at providing a trusted computing platform. Its goal is to guarantee that the software building the foundation of a system has never been altered or compromised. Without such a trusted basis all additionally provided protection measures (e.g. antivirus software or integrity checks) are void because an uncompromised state of the system cannot be ensured. On the ZYNQ-7000 ZC703 SoC this can be done by signing every partition included in the boot image with the private key of an asymmetric key pair. One after the other each component is authenticated, loaded and executed.
Protection Mechanisms
By choosing a ZC702 as a host platform different layers of protection can be applied. It provides a stack of algorithms aimed at providing confidentiality, integrity and source authentication. For each partition it can be decided individually how many layers should be added.
By using AES and HMAC confidentiality, integrity and source authentication can be provided. However, for each partition it can be decided individually whether RSA should be used for source authentication.
Deployment
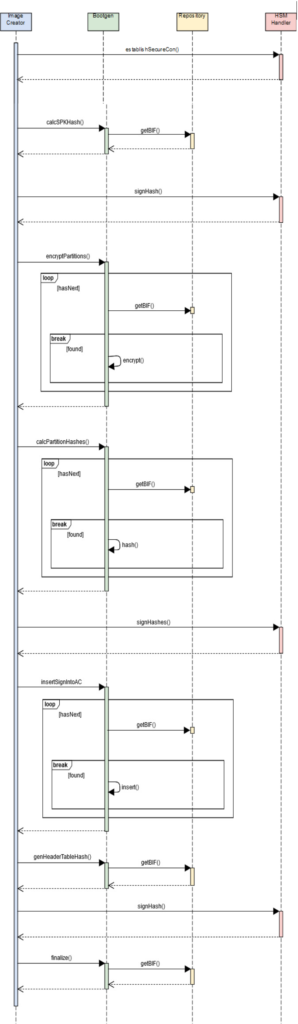
The main goal of the deployment process is to guarantee an efficient way of programming the Hardware Controllers. Therefore, a standardized process must be created that requires as little user interaction as possible. With the precondition that the operating system has already been built, this can be done in four interdependent steps. These in turn can be realized in different ways. Figure 3 shows the first of these four steps—the automated boot image creation.
Supervisor Dr. Andrew Paice
Award donor ABB Switzerland